Projects & Portfolio
Database & Business Intelligence
With proficiency in SQL, PL/SQL, T-SQL, and IBM Cognos, I optimize database structures and queries to improve performance and data retrieval efficiency. My experience in data analytics and business intelligence allows me to transform raw datasets into actionable insights, empowering organizations to make informed decisions.
Certified Cybersecurity & Network Security
Holding certifications such as CCNA, CCNP, CompTIA Security+, and Cisco Cybersecurity Certificate, I specialize in securing IT infrastructure, implementing risk mitigation strategies, and ensuring compliance with industry standards such as HIPAA and ISO 27001.
Innovative Problem Solving & Technical Leadership
I thrive in cross-functional environments, collaborating with security analysts, developers, and executives to align technology solutions with business objectives. Whether designing secure software, optimizing cloud security, or leading data-driven initiatives, I am committed to driving innovation and delivering technical excellence.
Dynamic Fifteen Puzzle Game
(HTML, CSS, JavaScript)
Designed and developed a browser-based Fifteen Puzzle Game featuring tile shuffling, animated movements, a cheat-solve algorithm, win detection, and customizable levels. Integrated dynamic background music, sound effects, and player score tracking, with support for multiple puzzle sizes and themes. Deployed and tested the game on GSU’s Codd server with in-teractive user feedback and bug tracking.
Healthiest Salad Website
This project is a fully responsive recipe website showcasing the world's healthiest foods, built entirely using HTML, CSS, and vanilla JavaScript. I designed the layout with accessibility and mobile-first principles in mind, added image optimization for performance, and implemented smooth CSS-based sliding effects for featured photos.
https://ahmedalaboodi83.github.io/healthiest-salad-site/recipe.html

GTSC Donations
This is a simulated phishing site created for a cybersecurity class at Georgia Tech.
It’s meant to show how fake login or donation pages can be used to trick people. Please don’t enter any real info this is for educational purposes only and nothing is stored.
Purpose:
Raise awareness of phishing tactics
Show how easy it is to spoof real websites
Promote safer online habits
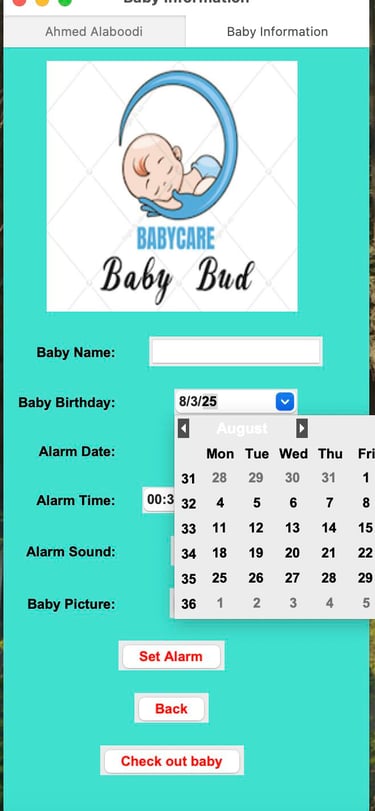
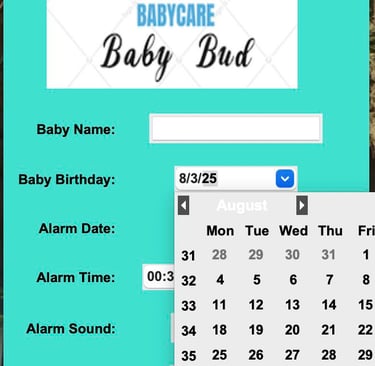
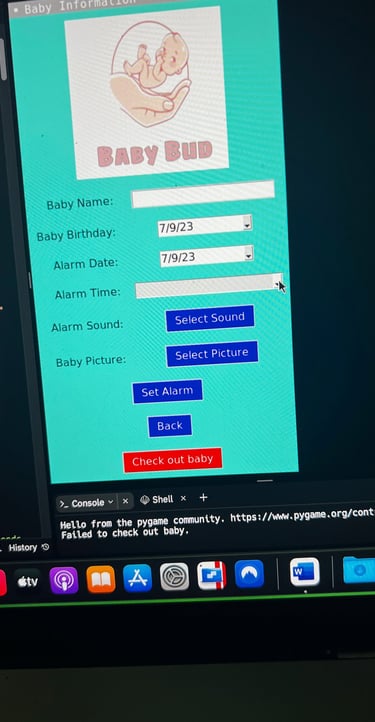
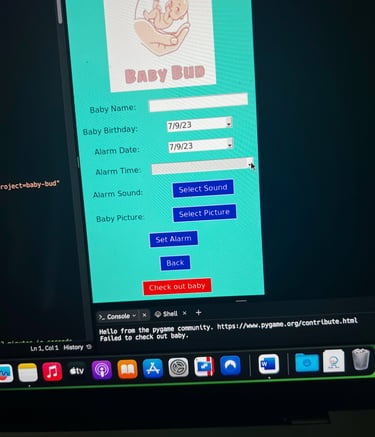
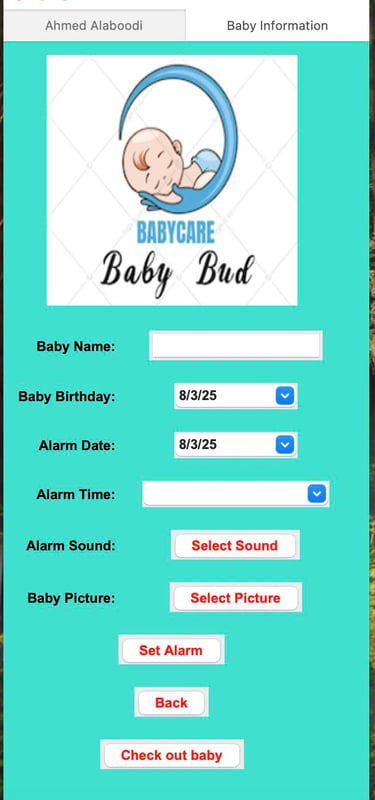
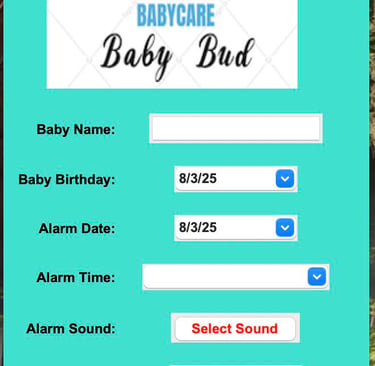
Baby Bud – Baby Care Alert & Tracker System
Full-Stack Baby Safety Tracker
Built a complete baby care and alert system using Python, Tkinter, and Firebase. Features include GPS tracking via Google Maps API, secure login with Firebase Auth, baby check-in/out, car registration, and custom audio/image alerts. Integrated real-time location display, alarm scheduling, and cloud data storage into one GUI-based solution focused on usability and safety.
Phone Number Tracker with Location & Spam Detection
Developed a Python-based phone number tracker that identifies the country, region, carrier, timezone, and validity of any global phone number using the `phonenumbers` and `geopy` libraries. The tool also includes a basic spam detection feature and generates a Google Maps link for approximate location visualization based on region data.
This project is designed to demonstrate real-world usage of Python for data parsing, API integration, geographic analysis, and data logging. It includes:
- Real-time input handling
- Scam/spam flagging (mocked, API-ready)
- Google Maps integration using geolocation
- Logging of number lookups into CSV
- CLI-based interface for portability
- Modular and extensible architecture
Cybersecurity Projects
Showcasing Ahmed's key contributions and technical expertise in cybersecurity.


Man-in-the-Middle (MITM)
Analyzed Layer 2–7 network traffic using Wireshark and PyShark to detect and interpret man-in-the-middle (MITM) attack patterns in real packet capture (PCAP) data. Leveraged network protocol analysis techniques to identify suspicious behaviors such as credential interception, unauthorized data transfers, and IRC communication. Developed Python scripts to automate traffic parsing and flag anomalous activity across multiple sessions. Strengthened skills in packet-level analysis, threat detection, and secure communication protocols.
Machine Learning in Cybersecurity
Python, scikit-learn, Pandas
Designed, trained, and deployed advanced classification models on real-world threat-intelligence datasets to automate de-tection workflows, improving identification accuracy and reducing mean time to detect threats.