About Ahmed Alaboodi
𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 & 𝐒𝐨𝐟𝐭𝐰𝐚𝐫𝐞 𝐃𝐞𝐯𝐞𝐥𝐨𝐩𝐦𝐞𝐧𝐭
I am a results-driven cybersecurity and software development professional with expertise in threat detection, risk mitigation, and secure application development. My background in software engineering, database management, and IT security allows me to develop robust, scalable solutions that enhance data integrity and system security. With hands-on experience in mobile and web application development, I bring a user-centric approach to technology, ensuring seamless functionality across platforms.
𝐃𝐚𝐭𝐚𝐛𝐚𝐬𝐞 & 𝐁𝐮𝐬𝐢𝐧𝐞𝐬𝐬 𝐈𝐧𝐭𝐞𝐥𝐥𝐢𝐠𝐞𝐧𝐜𝐞
With proficiency in SQL, PL/SQL, T-SQL, and IBM Cognos, I optimize database structures and queries to improve performance and data retrieval efficiency. My experience in data analytics and business intelligence allows me to transform raw datasets into actionable insights, empowering organizations to make informed decisions. At IBM, I designed complex data models and implemented high-performance Cognos solutions, streamlining data integration and reporting.
𝐂𝐞𝐫𝐭𝐢𝐟𝐢𝐞𝐝 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 & 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲
Holding certifications such as CCNA, CCNP, CompTIA Security+, and Cisco Cybersecurity Certificate, I specialize in securing IT infrastructure, implementing risk mitigation strategies, and ensuring compliance with industry standards such as HIPAA and ISO 27001. My knowledge of penetration testing, cloud security, and system administration helps organizations safeguard their critical assets from cyber threats.
𝐈𝐧𝐧𝐨𝐯𝐚𝐭𝐢𝐯𝐞 𝐏𝐫𝐨𝐛𝐥𝐞𝐦 𝐒𝐨𝐥𝐯𝐢𝐧𝐠 & 𝐓𝐞𝐜𝐡𝐧𝐢𝐜𝐚𝐥 𝐋𝐞𝐚𝐝𝐞𝐫𝐬𝐡𝐢𝐩
I thrive in cross-functional environments, collaborating with security analysts, developers, and executives to align technology solutions with business objectives. Whether designing secure software, optimizing cloud security, or leading data-driven initiatives, I am committed to driving innovation and delivering technical excellence. My passion for learning and adaptability allows me to stay ahead of emerging cybersecurity threats and software development trends.
𝐋𝐞𝐭’𝐬 𝐂𝐨𝐧𝐧𝐞𝐜𝐭!
I am always open to networking with professionals in cybersecurity, software development, and IT security. If you’re interested in discussing innovative solutions, industry trends, or potential collaborations, feel free to reach out!


How NAT works
Network Address Translation (NAT) is a fundamental technique used in networking that enables devices within a private network to communicate with external networks, such as the internet, by sharing a single public IP address. This process not only simplifies communication but also enhances security. Let’s break it down step by step!
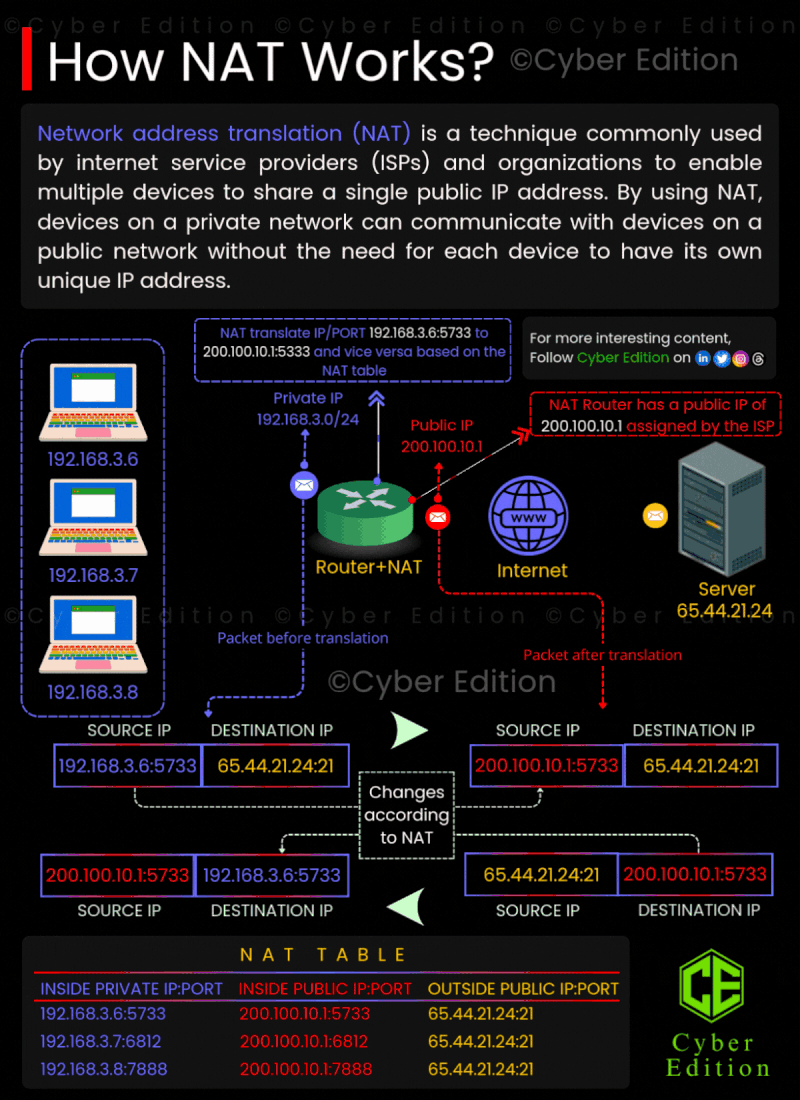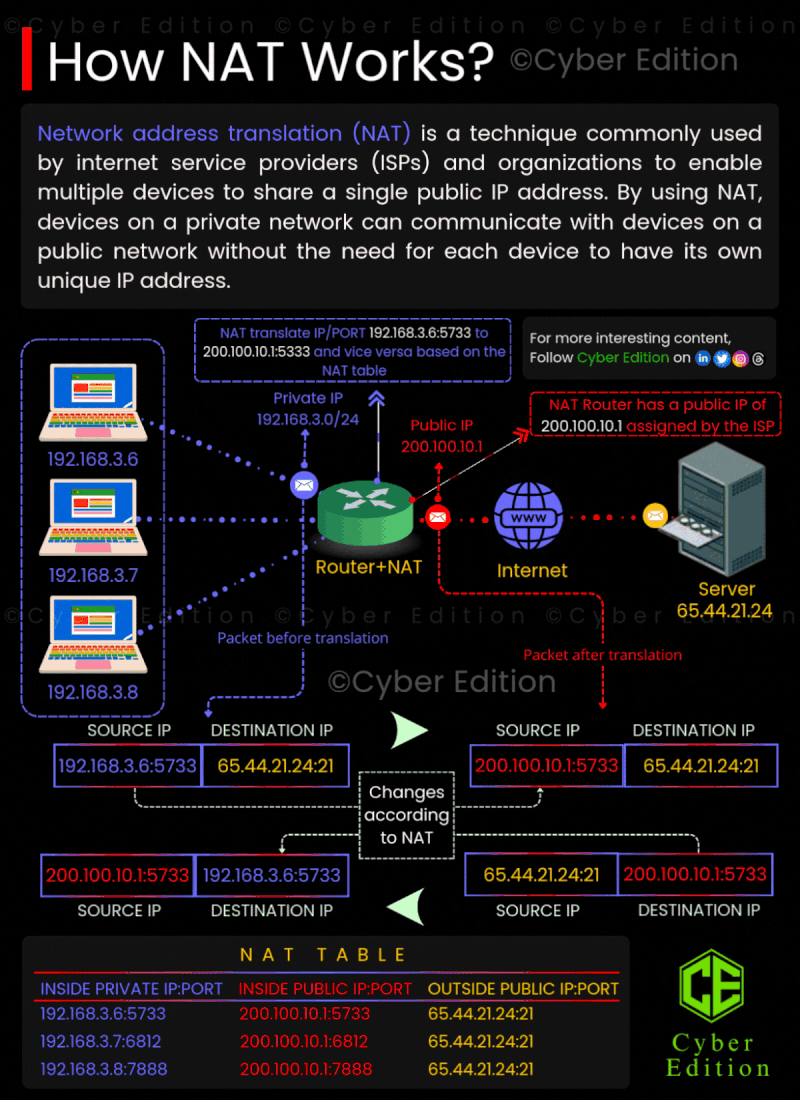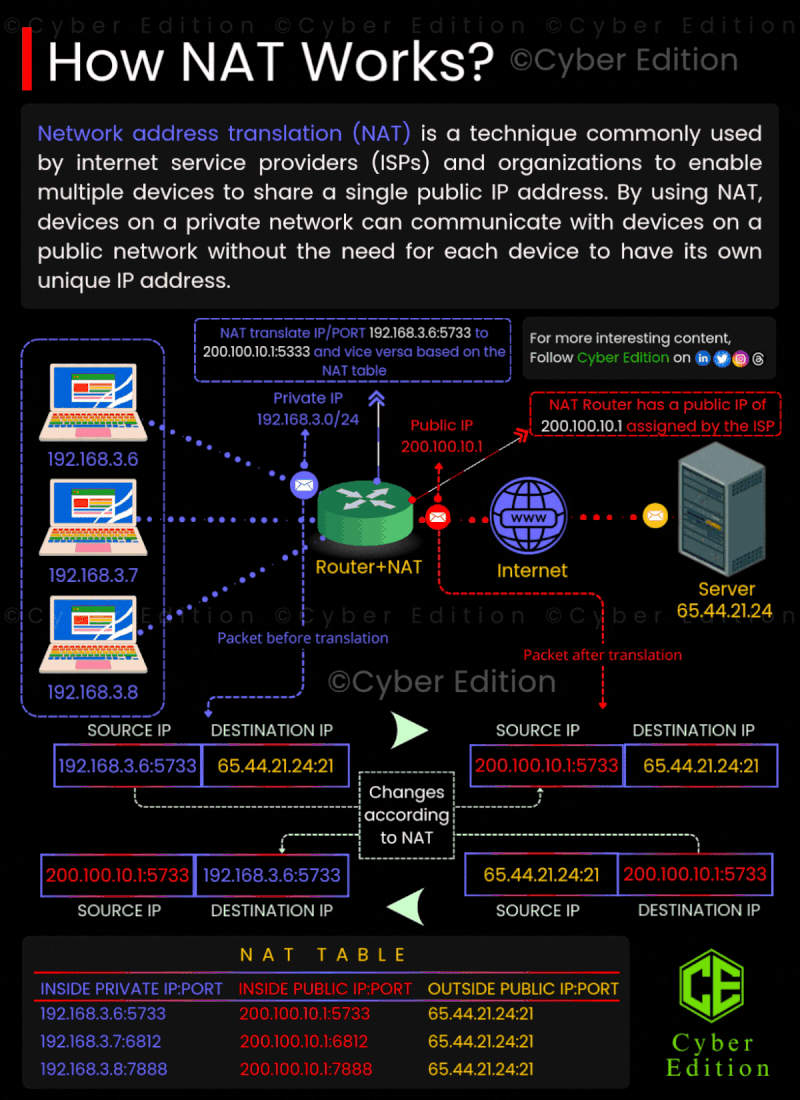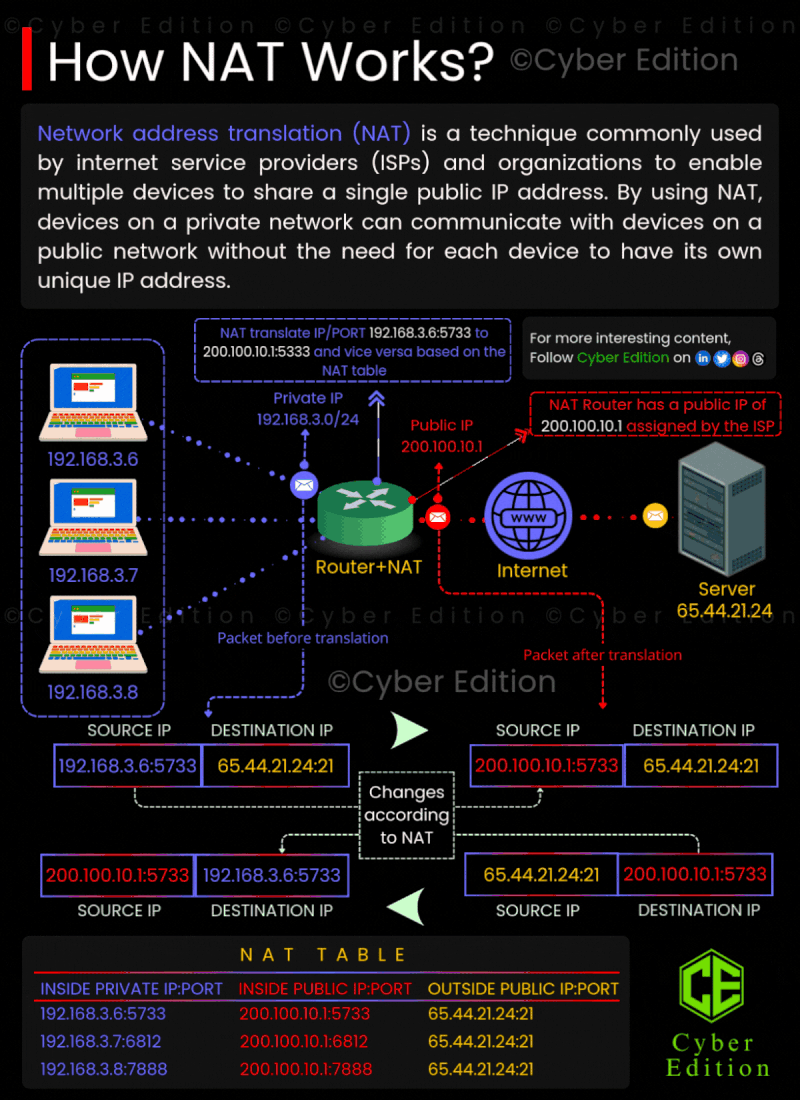
1: Private Network 🌍💻 Devices within a private network—such as those found in your home or office—utilize private IP addresses. These addresses, like 192.168.3.6, are not routable on the internet. Essentially, this means that these private IP addresses cannot directly communicate with external servers or services outside the local network. **Example:** Imagine a device on your home network with the IP address 192.168.3.6 that wants to access a website hosted on the internet. This device needs a way to connect to external servers without exposing its private IP address.
2: NAT Translates the IP 🔄🛠️ NAT comes into play at this juncture. When the device with the private IP (192.168.3.6) attempts to reach an external server, the NAT router intercepts the traffic. The router translates the private IP address to a public IP address. For instance, the router changes the address to something like 200.100.10.1. This public IP is what the internet recognizes. Since the communication is now associated with the public IP, the external server can respond back to that address. The NAT router keeps track of this mapping between the private and public IP addresses, ensuring that replies are sent back to the correct device inside the private network.
3: Communication Happens 🌐🔄 Once the NAT router has translated the private IP to the public IP, the device can now send its request to the internet. The website or server will respond to the public IP address, which the NAT router receives. The router then translates the public IP address back to the original private IP address and directs the response to the correct device within the private network.
4: Security and Privacy 🔒🕵️♂️ One of the crucial benefits of NAT is the added layer of security it provides. Since the internal IP addresses are not visible to external networks, it becomes more challenging for potential attackers to reach devices on the private network. NAT acts as a barrier between the internal private network and the larger internet, providing a semblance of anonymity.
5: Address Conservation 📉💻 NAT also plays a significant role in address conservation. With the ever-growing number of devices, available IPv4 addresses are becoming scarce. By allowing multiple devices in a local network to share a single public IP address, NAT helps in managing the limited pool of IP addresses efficiently. In conclusion, NAT is an essential technique for managing the communication between private networks and the external internet. By translating private IP addresses to a single public IP, it not only eases connectivity but also enhances security and optimizes the use of IP addresses. Understanding how NAT works can give you insights into better managing your home or office network!